Net-Peeker 4.5.0.1431 Personal Edition + Cracked.dll | 12.46 MB
NetPeeker is a network monitor and control tool for personal Internet user.By revealing all applications accessing network and their connections, showing speed in real time, you can find more hidden information about your network.The build-in personal firewall protect you from hackers’ attack from outside.
You can find those "Spyware" or "Trojan" and block them.
You can kill connections you don’t want without shutdown the application.
You can trace back to the source to find who is the guy and report abuse.
You can setup speed throttle to limit network bandwidth usage for every application and every connection, and also can guarantee bandwidth for critical applications
Build-in filter can kill most popup window for you when you surf Internet, it can even kill those "flying windows" which cannot be killed by other popup killer.Main Features
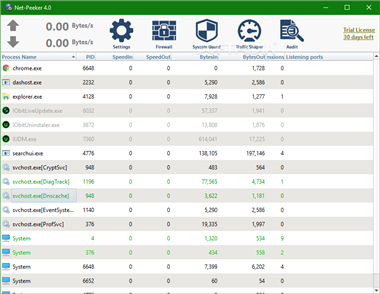
Distributed network traffic monitor
Display real time network traffic speed for every computer in the network.
Display all active network applications on any computer in the network.
Display all sessions and listen to all ports for any active network application on any computer.
Display application properties and loaded modules.
Support "Internet Connection Sharing (ICS)", and can monitor network usage of ICS clients without installing the NetPeeker agent in the clients.
Can monitor NETBIOS file transfer, which is copying shared files inside a local network.
Use "WHOIS" service to get detailed information on selected remote IP addresses and domain names.Desktop based firewall on all computers
Integrated system firewall and application firewall.
Support rules on applications, IP addresses/port numbers, remote country, DNS names, protocol types, and even HTTP URLs.
Rule-Exception mode rule structure for easier setup and understandable rule relations.
Support rule schedule, and can specify the effective time range for every firewall rule.
Fast firewall engine which can handle thousands of rules at the same time.
Drop invalid network packets.
Detect and block port scans, SYN floods, and DOS attacks.
Stealth mode to hide your computer from hackers.
Support importing spyware rules from BlueTack or Sponge, which have excellent anti-spyware rule listsLimit network speed on all computers
Rule based network speed shaping. Rules can be specified on applications, IP addresses/port numbers, remote country, DNS names, protocol types, and even HTTP URLs.
Support rule schedule, can specify the effective time range for every speed limit rule.
"throttle priority" feature, which allow you to give critical applications or remote sites more bandwidth.
Network traffic quota, specify monthly/daily network usage quota before block or limit speedProtect system against "Malwares"
Protect system by monitoring system operations, deny operation by rules. Can be used to prevent malware from running
Rule on registry operations can specify detailed access type
Rule on execution operations can specify the command line argument
For all rules, "actor"(parent process) can be specified to refine the rule.Log and analyze network traffic
Log every session, including start/stop time, applications, remote addresses/ports, total transferred bytes and average speed.
Generate network traffic statistics report, and display period network usage for every application and every remote IP.
Store log information in compact mode to save disk space.
Support archiving on the fly, archive log files from remote agents, and save the files in .ZIP format.
Load archived log files without uncompressing the archive.
Support exporting log information into text format.Capture network traffic
Live capture network packets for any active network application or session.
Support pre-defined capture filter on applications, and use filter to get packets on appointed applications and remote addresses.
Associate captured packets with session logs, so you can browse captured packets while browsing logged sessions.
Support exporting captured packets into TCPDUMP format, so it can be further analyzed using third-part tools.
Support archiving on the fly, to archive captured files from remote agents, and save in .ZIP format.
Load archived capture files without uncompressing.




